As the healthcare industry rapidly transitions into the digital world, the need for securing sensitive health information has never been more critical. In the U.S., the Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, establishes rigorous standards to ensure the privacy and security of patient data.
With the increasing use of electronic health records (EHRs), HIPAA compliance is more important than ever. Ensuring compliance not only builds trust but also shields organizations from severe penalties. This article explores practical steps for achieving HIPAA compliance, with a focus on AWS as a secure and scalable solution for healthcare applications.
Protecting Patient Data: A Critical Priority
Patient care may be at the forefront of healthcare organizations, but protecting patient data is just as vital. At JetBase, we handle large amounts of personal health data, and safeguarding it remains a top priority in every project we undertake. Under HIPAA, this sensitive information is referred to as Protected Health Information (PHI), which includes any data that can be used to identify a patient.
HIPAA outlines 18 specific identifiers that fall under PHI. These identifiers include traditional information like medical records and lab results. However, with the evolving nature of digital health data, experts are advocating for the inclusion of newer categories—such as social media activity and LGBTQ+ status—under modern privacy standards.
Examples of PHI under HIPAA regulations:
- Name
- Address (down to street level)
- Dates related to the individual (birthdays, admissions, discharges, death)
- Telephone numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health plan beneficiary numbers
- Device identifiers and serial numbers
- IP addresses
- Biometric data (fingerprints, voice prints)
- Full-face photographs
- Unique identifying numbers or characteristics
The Rising Threat of Data Breaches
Despite HIPAA's clear standards for protecting PHI, healthcare organizations continue to face risks from data breaches, often due to non-compliance with these regulations. Since 2009, multiple high-profile breaches have exposed sensitive patient information and led to significant consequences.
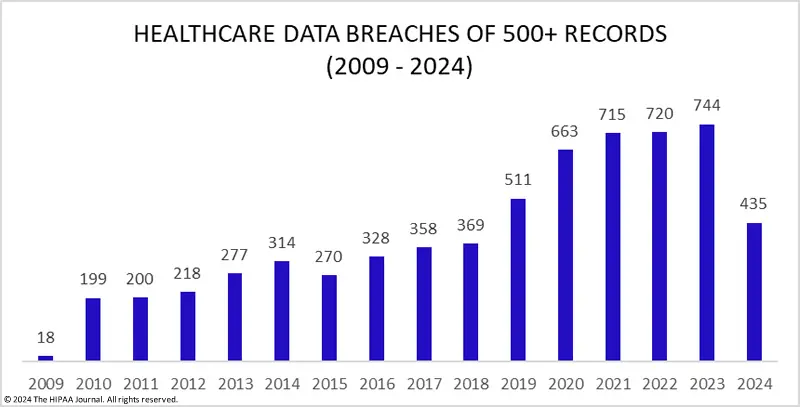
The most common HIPAA violations leading to breaches include:
- Unauthorized access to healthcare records
- Failure to conduct organization-wide risk analysis
- Poor risk management practices
- Delays in providing patients access to their health records
- Lack of a HIPAA-compliant Business Associate Agreement (BAA)
- Inadequate access controls for ePHI
- Failure to encrypt data or apply equivalent protections
- Delayed breach notifications (exceeding the 60-day limit)
- Unauthorized disclosure of PHI
- Improper disposal of PHI
Consequences of HIPAA Violations
HIPAA violations have serious repercussions. Fines can range from thousands to billions of dollars, depending on the severity and scale of the violation. The Department of Health and Human Services' Office for Civil Rights (OCR) is responsible for issuing penalties, but in some cases, violations result in technical assistance or corrective action plans.
For instance, in 2022, Oklahoma State University – Center for Health Sciences was fined $875,000 after failing to perform a risk analysis, report security incidents, and issue proper breach notifications. This affected 279,865 individuals. Another case in 2024 saw Montefiore Medical Center fined $4,750,000 for failing to conduct a comprehensive risk analysis and neglecting to monitor systems containing ePHI.
Moreover, Kaiser Foundation Health Plan Inc. is currently under investigation for disclosing the data of 13.4 million individuals to third parties (such as Microsoft and Google) through tracking technologies on its websites and apps. This is poised to become the largest healthcare data breach to date.
Mitigating Risk and Ensuring Compliance
Healthcare organizations must adopt proactive measures to avoid HIPAA violations and ensure patient data security. By staying vigilant, healthcare organizations can avoid costly breaches while maintaining patient trust
Measures to avoid HIPAA violations:
| Regular risk assessments are essential for identifying potential vulnerabilities. | Implementing strong encryption protocols for all ePHI, whether in transit or at rest, is equally critical. | Limiting access to PHI based on job roles and conducting ongoing staff training on HIPAA compliance are fundamental practices. | Conduct routine audits to ensure that all systems adhere to HIPAA's security framework. |
Key Strategies for Keeping Patient Data Secure and Ensuring HIPAA Compliance
Cloud solutions like AWS provide healthcare organizations with the flexibility, scalability, and security needed to meet HIPAA requirements. AWS operates on a shared responsibility model, where it provides the secure infrastructure while customers are responsible for configuring and managing services securely. By leveraging AWS, healthcare organizations can build secure and compliant healthcare applications efficiently.
HIPAA Compliance Checklist for Protecting Personal Health Information:
- Educate Healthcare Staff
Provide regular training on HIPAA regulations and the importance of safeguarding PHI. - Restrict Access to Data and Applications
Limit access to PHI only to authorized individuals who need it to perform their jobs. - Implement Data Usage Controls
Establish clear policies on the use, sharing, and transmission of PHI. - Log and Monitor System Activity
Maintain detailed records of who accesses PHI, and regularly review these logs for suspicious activity. - Encrypt Sensitive Data
Use encryption to protect PHI, both when stored and transmitted. - Secure Mobile Devices
Ensure that mobile devices used to access or store PHI are properly secured, using methods such as encryption and remote wipe capabilities. - Mitigate Risks from Connected Devices
Protect network-connected devices, such as medical equipment, from unauthorized access. - Conduct Regular Risk Assessments
Perform routine evaluations to identify and address vulnerabilities in your systems and processes. - Utilize Off-Site Data Backup
Regularly backup PHI data and store it securely off-site to ensure recovery in case of data loss. - Evaluate the Compliance of Business Associates
Ensure that all third-party partners are HIPAA-compliant and have signed business associate agreements.
Adhering to this checklist is key to maintaining both regulatory compliance and patient trust in the security of their personal health data.
AWS and Its Shared Responsibility Model for HIPAA Compliance
AWS is a trusted, secure, and scalable cloud solution for healthcare applications, providing low-cost IT infrastructure that aligns with HIPAA compliance requirements. With its shared responsibility model, AWS enables healthcare organizations to build applications that safeguard protected health information (PHI) effectively. Below are five essential steps for creating HIPAA-compliant applications using AWS.
1. Become a Business Associate (BA)
In the healthcare ecosystem, covered entities (such as clinics or insurance companies) and third-party partners (e.g., IT providers or development teams) handle PHI differently under HIPAA regulations. A Business Associate Agreement (BAA) is a legal arrangement that defines each party's responsibilities concerning PHI. If you're developing a healthcare project, ensure you qualify as a business associate and have established a BAA with both the covered entity and AWS as your cloud provider. This agreement outlines roles and obligations to ensure all parties adhere to HIPAA regulations.
Learn more about BAAs here.
2. Use Only HIPAA-Eligible AWS Services
AWS provides a list of HIPAA-eligible services that comply with the necessary security controls and contractual requirements for handling PHI. It is crucial to stick to these services when developing healthcare applications to maintain compliance. While you can use any AWS service in a HIPAA-designated account, only those listed as HIPAA-eligible should be used to process, store, or transmit PHI.
“Whenever we integrate third-party services into our applications, we ensure they meet HIPAA eligibility standards, prioritizing security and compliance at every step.”
— Shuhrat, Full Stack Developer at JetBase
To stay up to date on eligible services, refer to the HIPAA Eligible Services Reference for the latest offerings. These services have been verified to meet HIPAA standards for privacy and security.
3. Enable Encryption for Data in Transit and at Rest
Data encryption is a fundamental requirement for securing PHI on AWS. Ensure all PHI is encrypted both in transit and at rest. For data at rest, use services such as S3 bucket encryption, EBS volume encryption, and RDS database encryption. For data in transit, enforce SSL/TLS connections to secure the transmission.
AWS offers encryption tools like AWS Key Management Service (KMS), AWS CloudHSM, and AWS Certificate Manager (ACM) to help you implement robust encryption strategies. Additionally, ensure you manage secrets and API keys securely and rotate them regularly to mitigate security risks.
“We ensure that all data is encrypted both in transit and at rest. With AWS, it's incredibly simple—just a few clicks.”
— Shuhrat, Full Stack Developer at JetBase
4. Conduct Regular Audits and Risk Assessments
Maintaining HIPAA compliance in AWS requires ongoing audits, risk assessments, and policy reviews. Annual assessments help identify system vulnerabilities, conduct gap analysis, and implement appropriate risk mitigation controls. Regularly test these controls through penetration testing, breach simulations, and security scans to ensure they are effective.
All AWS services handling PHI should be audited routinely, and any deployment issues identified and resolved promptly. Simulated breach exercises can also help evaluate the effectiveness of your incident response plan. Tools such as AWS CloudTrail and AWS Trusted Advisor are invaluable for monitoring security, access control, and detecting unusual activity.
![Cloud Software Development [AWS].webp](/static/Cloud_Software_Development_AWS_a351611d38.webp)
To sum up — Key Recommendations for HIPAA Compliance and Reliable Patient Data Storage in Healthcare Projects
As an IT provider specializing in healthcare development, we understand that ensuring HIPAA compliance and reliable patient data storage is not only a regulatory obligation but a key component of patient trust. Choosing a cloud provider like AWS, which offers HIPAA-compliant services, is an important step. However, it's equally essential to sign a Business Associate Agreement (BAA), which ensures that all parties involved in handling PHI adhere to HIPAA’s rigorous standards.
If you’re embarking on your healthcare IT journey, JetBase is here to provide expert guidance and ensure your HIPAA compliance. With our deep knowledge of digital healthcare solutions and a commitment to security, we can help you navigate the complexities of patient data protection. Contact us today for more information and a free consultation.
Protect your organization and your patients by partnering with experts who prioritize security and compliance in every solution. Don't wait until a breach happens—get started with JetBase today!